Crypto Report #0135 Solana Wallets Drained: Over 650 Accounts Hit in Single-Day Attack (October 9, 2025)
Keywords
crypto theft, solana, pump.fun, raydium, deQzbGSDA3U6bFmxAfWuJYhYBvN647fP1i8DEDoVNW3
Abstract
On October 9, 2025 657 wallets were fully drained and all SOL coins were transferred to deQzbGSDA3U6bFmxAfWuJYhYBvN647fP1i8DEDoVNW3
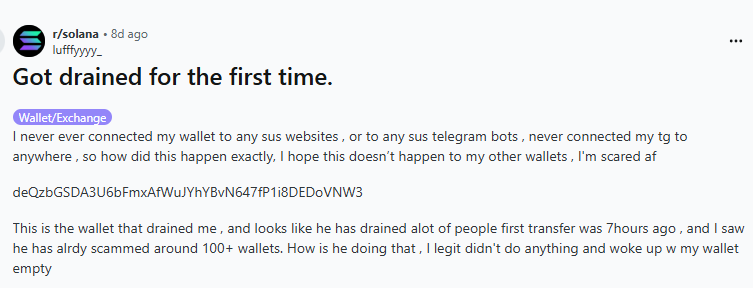
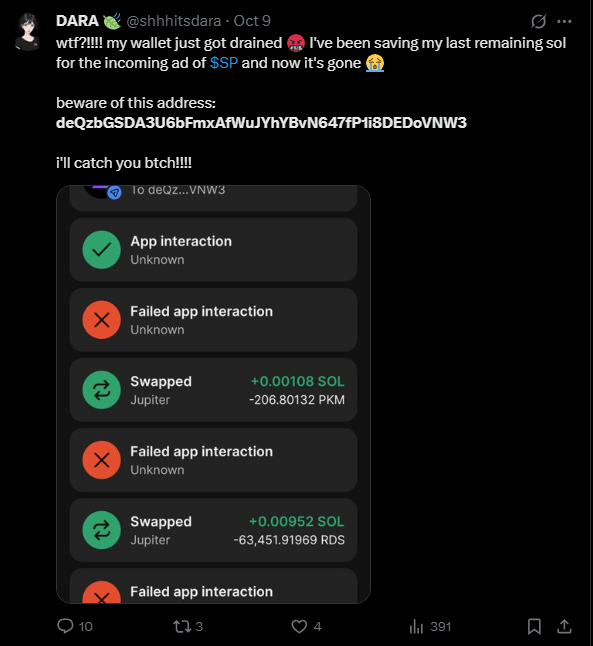
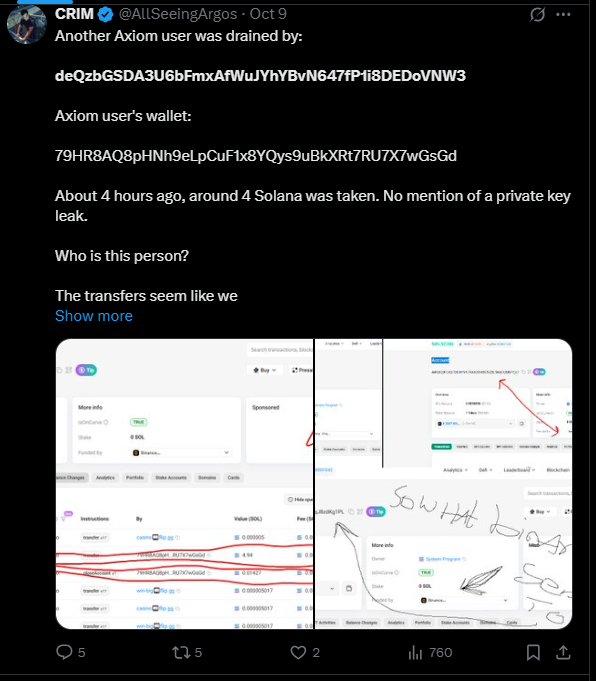
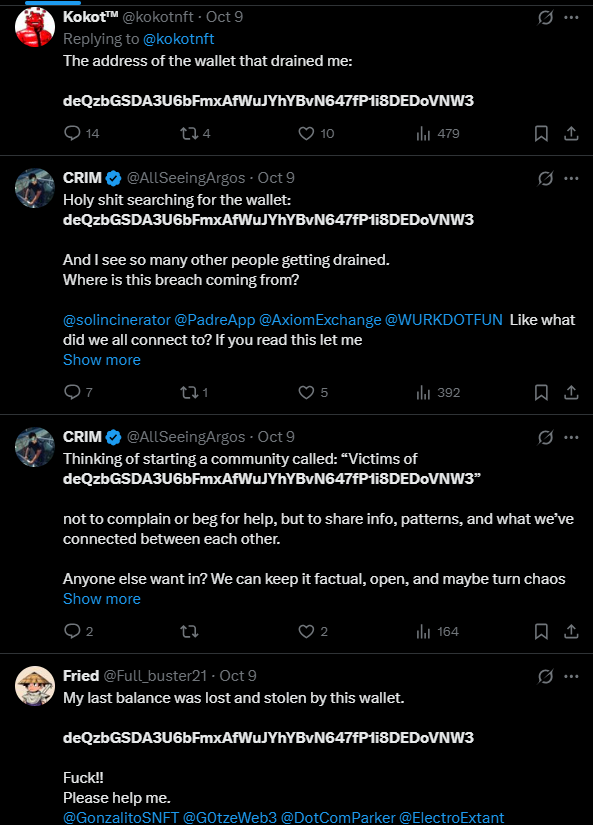
The material of investigation
- Solana explorer
- Downloaded and uploaded into PostgreSQL the transaction history of 655 compromised wallets (3,782,452 transaction records in the table
transaction_data) - Manual table
address_solnamecontains Solana public names of most used addresses by compromised wallets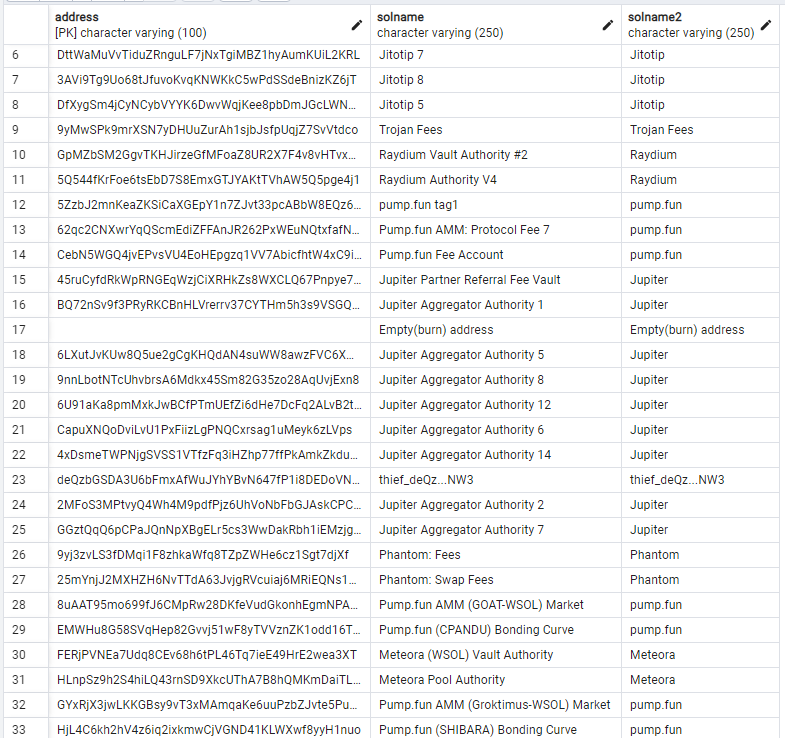
- The full backup of the analytics PostgreSQL database can be downloaded here for your own investigation
Analytics
Stats
- 657 Solana wallets were drained from Oct 09, 2025 00:00 till Oct 09, 2025 17:40 (17 hours attack)
- Only SOL coins were drained and transferred to the Solana wallet deQzbGSDA3U6bFmxAfWuJYhYBvN647fP1i8DEDoVNW3
- 669 drain transfers (some wallets were drained twice)
- Total amount of stolen coins 97.05 SOL (around $20,000)
- Average amount per compromised wallet is $33, the max is $1,077.98 for one account
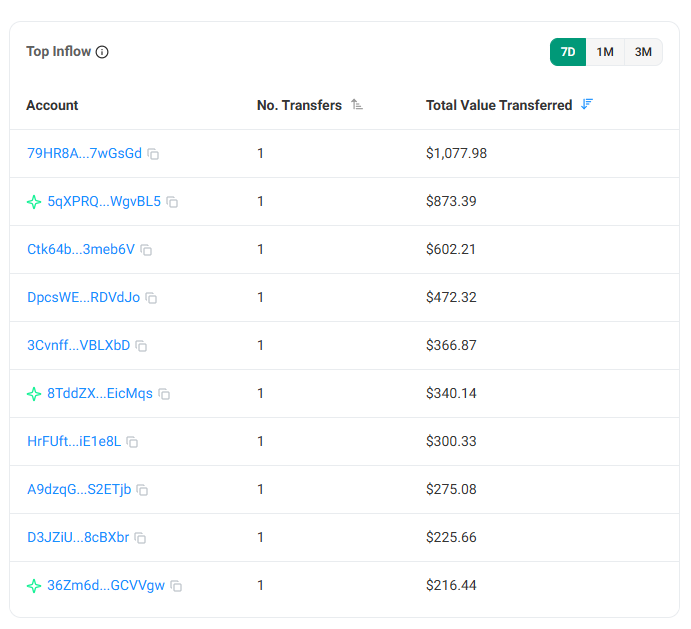
The attack was planned and started at midnight, the scenario of the attack is the same:
- calling the closeAccount function to return all available rent SOL to the main victim wallet
- drain all SOL coins and transfer them to a malicious wallet
deQzbGSDA3U6bFmxAfWuJYhYBvN647fP1i8DEDoVNW3remaining SOL amount reduced to <$1 - 12 of 657 accounts were drained twice
select count(*), from_address from transaction_data where to_address = 'deQzbGSDA3U6bFmxAfWuJYhYBvN647fP1i8DEDoVNW3' and root != 'deQzbGSDA3U6bFmxAfWuJYhYBvN647fP1i8DEDoVNW3' group by from_address order by count(*) desc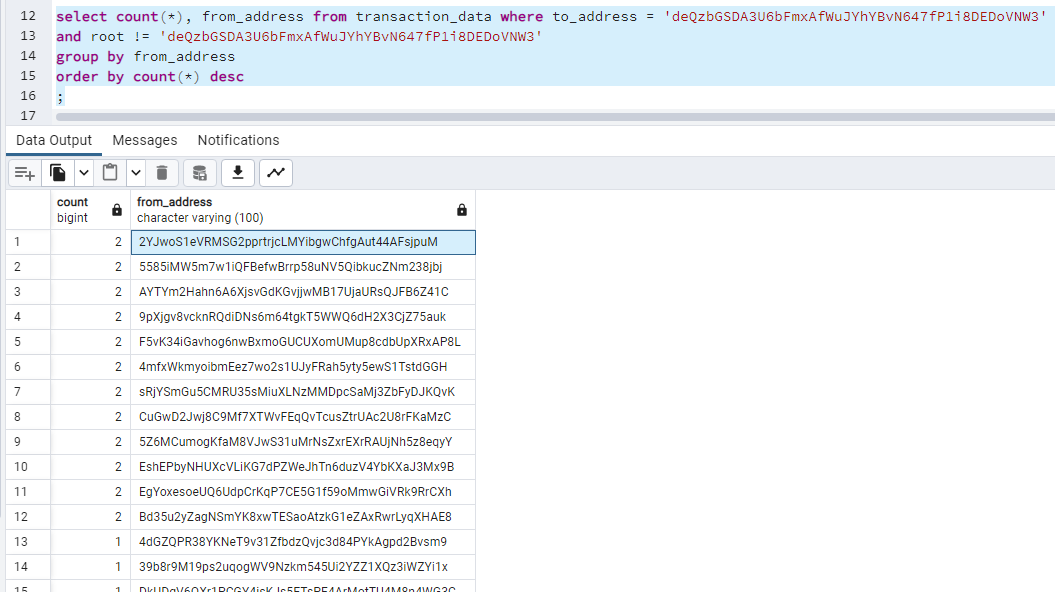
pump.fun smart contracts
- 96% of all the compromised wallets sent money to pump.fun smart contracts in their history, 94% to Raydium DEX
select COUNT(*), solname2, (100*COUNT(*)/655) as Percent from ( select distinct root, from_address, COALESCE((select solname2 from address_solname where address = to_address limit 1), to_address) as solname2, action, flow from transaction_data )s where flow = 'out' and root <> 'deQzbGSDA3U6bFmxAfWuJYhYBvN647fP1i8DEDoVNW3' group by solname2, flow having count(*) > 1 order by count(*) desc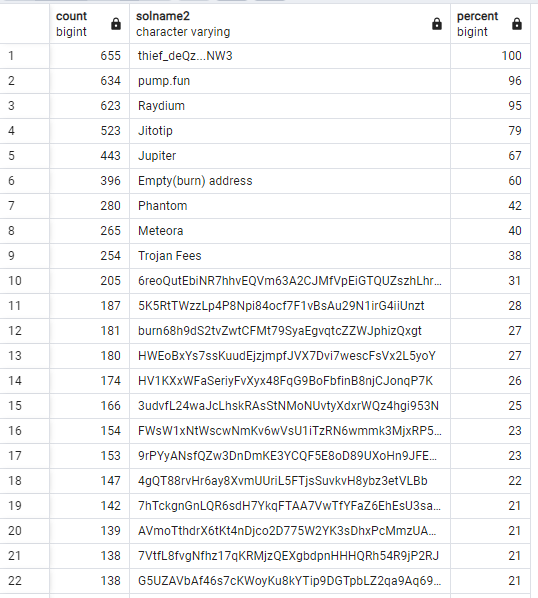
- The most used addresses:
- 92% of compromised wallets sent coins to
comp5Q544fKrFoe6tsEbD7S8EmxGTJYAKtTVhAW5Q5pge4j1(Raydium Authority V4) - 86% to
5ZzbJ2mnKeaZKSiCaXGEpY1n7ZJvt33pcABbW8EQz6Dg(pump.fun tag1)select COUNT(*), solname, to_address, (100*COUNT(*)/655) as Percent from ( select distinct root, from_address, COALESCE((select solname from address_solname where address = to_address limit 1), to_address) as solname, to_address, action, flow from transaction_data )s where flow = 'out' and root <> 'deQzbGSDA3U6bFmxAfWuJYhYBvN647fP1i8DEDoVNW3' group by solname, to_address, flow having count(*) > 1 order by count(*) desc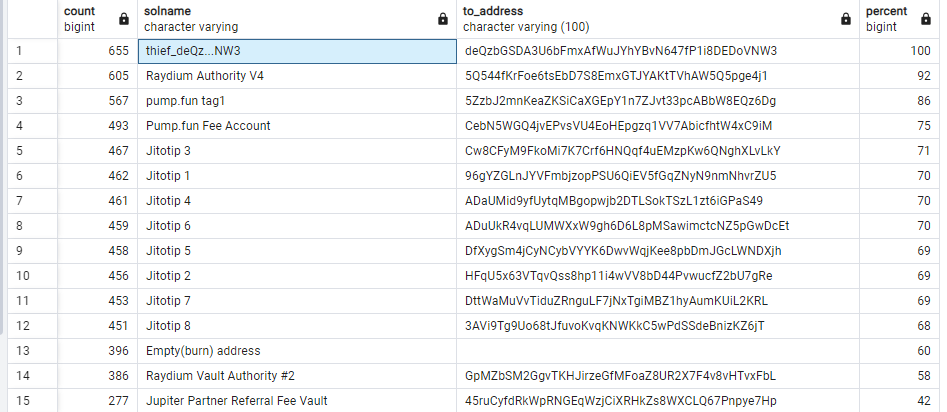
- 92% of compromised wallets sent coins to
Conclusions
- Victim wallet private keys were compromised, evidenced by direct wallet-to-wallet transfers without DeFi interactions
- The attack targeted a specific set of wallets, an attacker may collect another set of wallets
- The private keys were most likely compromised via malicious code on pump.fun or Raydium DEX
- Recommendation: Immediately transfer all assets from compromised wallets to new, secure wallets
- Check if your wallet appears on the list of compromised addresses
This investigation is ongoing…
If you have additional information or insights, please reach out at https://x.com/cryptokarl013